There are 2 forms of system access control: Bodily and rational. Actual physical access control limits access to campuses, properties, rooms and physical IT belongings. Logical access control limitations connections to Laptop networks, system documents and details.
Exactly what is a company password supervisor? Business password supervisor like LastPass has two key parts:
What's the distinction between Bodily and reasonable access control? Access control selectively regulates who is permitted to check out and use specific spaces or information. There are 2 varieties of access control: physical and reasonable.
Precisely what is an IP Address? Consider each individual gadget on-line like a household. That you should deliver a letter to a colleague residing in 1 of those properties, you will need their dwelling address.
Here is the overall course of action involved with securing access and managing access control inside of a company.
Access control guidelines is usually built to grant access, Restrict access with session controls, as well as block access—everything relies on the desires of your enterprise.
What's more, it complicates the whole process of onboarding and offboarding personnel, as modifications in one system might not be mirrored in Some others.
Centralization of identification management: IAM centralizes and simplifies the administration of consumer identities. It provides a framework for managing digital identities and access legal rights, guaranteeing that only approved folks can access the best assets at the correct instances for the proper good reasons.
RBAC will allow access based upon The task title. RBAC mainly gets rid of discretion when offering access to things. One example is, a human sources professional should not have permissions to develop network accounts; This could be a role reserved for community administrators.
MAC grants or denies access system access control to useful resource objects based upon the data protection clearance of your person or machine. For instance, Security-Increased Linux is an implementation of MAC on a Linux filesystem.
Authorization follows successful authentication. It involves granting or denying access depending on the consumer’s or system’s privileges. The privileges are predefined and dictate what assets the consumer or system can access and also to what extent.
Find out more Access control for faculties Present a straightforward sign-on expertise for college students and caregivers and preserve their private information Harmless.
Identity and access management answers can simplify the administration of these guidelines—but recognizing the need to govern how and when facts is accessed is the initial step.
One particular of those problems is handling multi-tenancy. Multi-tenancy refers to the condition where by multiple users or groups share the identical application instance, Every with their own independent and protected access.
 Marla Sokoloff Then & Now!
Marla Sokoloff Then & Now!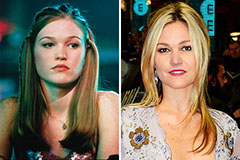 Julia Stiles Then & Now!
Julia Stiles Then & Now!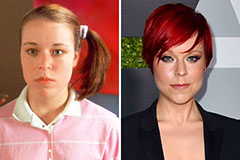 Tina Majorino Then & Now!
Tina Majorino Then & Now! Lucy Lawless Then & Now!
Lucy Lawless Then & Now! Morgan Fairchild Then & Now!
Morgan Fairchild Then & Now!